Defending Against Malware Sandbox Evasion: A Linux User’s Guide
In the cat-and-mouse game of cybersecurity, malware authors constantly evolve their tactics to slip past our defenses. One particularly cunning strategy is sandbox evasion, where malicious code behaves innocently when it suspects it’s being monitored, only to unleash its true nature on your actual system. This post demystifies these evasion techniques and equips you with practical defenses for your everyday Linux system—no paranoia required.
Why Sandbox Evasion Matters (Even for Daily Users)
Sandbox evasion might sound like an esoteric concern for security researchers, but it has real implications for regular users. Many security tools—from email providers to antivirus software—use sandboxes to test suspicious files. When malware can recognize these controlled environments, it can play dead during scanning but activate later on your real system.
Consider this scenario: you download a seemingly harmless app and run it in a virtual machine (VM) or sandbox to be safe. It behaves nicely for a few minutes, so you assume it’s clean. But once on your real system, it suddenly springs into action – because it was engineered to detect the VM and wait.
This isn’t theoretical paranoia. The Beep information-stealer discovered in 2023 comes loaded with 17 different evasion techniques – it can obfuscate its code, detect if it’s being debugged or traced, disable monitoring tools, and more. Such sophisticated malware is becoming increasingly common.
So while you might ask, “I’m not a malware analyst, do I really need to worry about sandbox evasion on my personal machine?” the answer is yes—everyday threats are adopting these tricks, and understanding them is your first line of defense.
Common Evasion Techniques (With Examples)
Let’s explore the most common tactics malware uses to avoid detection:
1. Delayed Execution (Playing the Waiting Game)
One straightforward way malware evades sandbox analysis is by simply not doing anything suspicious for a while. Sandboxes typically only observe a program for a short period (often a few minutes). Malware authors exploit this by inserting deliberate delays or idle loops so that the real payload activates after the sandbox timeout.
Real-world example: The GoldenSpy malware’s installer famously waited a full two hours before installing its malicious payload, long after many sandbox analyses would have finished. Other malware uses “API flooding,” calling thousands of benign system calls in a loop to slow down execution and outlast the sandbox’s patience.
Some advanced sandbox solutions try to counter this by fast-forwarding time or cutting sleeps short. In response, malware like the Kovter family uses high-resolution timers like GetTickCount in Windows to detect if a sandbox artificially accelerated the clock. If the timing doesn’t add up (say, 10 minutes of sleep elapsed in only 10 seconds of real time), the malware knows it’s under analysis and may terminate or skip malicious actions.
2. Environment Checks (Peeking Behind the Curtain)
Another evasion tactic is for malware to check the environment it’s running in. The goal is to detect telltale signs of a virtual machine, sandbox service, or researcher’s analysis rig – and if found, abort or conceal malicious behavior. It’s like a burglar checking for security cameras before deciding to break in.
Malware performs various system checks to determine if it’s in a real user’s system:
-
Hardware inspection: Looking at CPU cores, available memory, or BIOS/Vendor identifiers – unusual values can reveal a VM. Many sandboxes run with a single CPU core or have generic BIOS strings like “VMWARE” that malware knows to look for.
-
Artifact detection: Searching for specific drivers, services, or registry keys associated with popular sandbox/VM platforms.
-
Process enumeration: Looking for processes named after analysis tools (like wireshark.exe or vboxservice) or checking if typical user programs are missing.
Real-world example: APT28’s CHOPSTICK backdoor would completely stop its execution if it detected it was running in a sandbox environment – essentially a built-in self-destruct if the coast wasn’t clear.
Some malware goes to creative lengths with these checks, probing physical characteristics like the system’s temperature sensors or battery status, as a VM might not report realistic values. Others check for “human” activity or system uptime (did the machine boot just 1 minute ago? Probably a sandbox).
3. User Interaction Detection (Are We There Yet?)
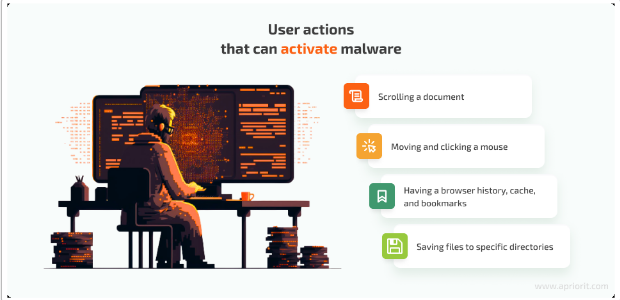
One big difference between a sandbox and a real user’s PC is user activity. Automated sandboxes typically execute malware in a vacuum – no mouse moving, no typing, no windows being clicked – whereas a real user will be clicking, typing, browsing, and so on. Malware can exploit this difference by programming itself to remain dormant until it observes normal user interaction.
Implementation examples:
-
Some malicious documents only execute their payload after a user scrolls to a certain part of the document or clicks a prompt. If you open an infected Word or PDF and just leave it, nothing happens – but the moment you scroll down or click an embedded object, the trap is sprung.
-
Others monitor mouse movement or keystroke events. An absence of mouse movement, or movement that is too perfectly linear or fast (as might be generated by a script), can be a sign of automation.
-
Some strains check the speed and frequency of mouse clicks – if it’s impossibly fast or there are zero clicks in, say, 5 minutes after launch, it might assume it’s in a sandbox and stay quiet.
Real-world examples: - The DarkHotel APT malware was reported to repeatedly check the mouse cursor position to determine if a real person was using the machine. - The Tinba banking trojan specifically watched for mouse movements and screen activity, only proceeding when user activity was detected. It literally “waited for the mouse” before doing its dirty work.
This tactic explains why malware might appear inert when first opened, lulling you into a false sense of security until you engage with it.
4. Process and File Scanning (Case the Joint)
Malware often scans the system’s processes and files as an early step, both to orient itself and to find signs of a monitored environment. This gives it information to decide its next move.
Common scanning methods include:
-
Searching for security processes: Malware may enumerate running processes to identify known security tools. If it finds an EDR (Endpoint Detection & Response) agent or popular analysis tools (e.g., process monitors, debuggers) it might shut down or disable certain functions. Some malware look specifically for sandbox agent processes or DLLs and will exit if they’re present.
-
Checking the file system: Malware might check if the user’s Documents or Downloads directories have typical files, or if the browser has a history database. No browser cache or bookmarks might indicate a fresh sandbox image.
-
Looking for competition: It may scan for other malware or rootkits (some malware will quit if it finds certain other malware, to avoid conflicts or attention).
Real-world example: The Beep malware not only had multiple evasion techniques but could explicitly turn off debuggers and hide or disable certain APIs when it sensed it was being analyzed.
5. Code Injection (Hiding in Legit Processes)
Code injection is an evasion and persistence tactic where malware doesn’t keep all its evil deeds in its own process. Instead, it inserts malicious code into another process’s memory or even starts a new process in a hollowed-out state. This helps it blend in behind legitimate process names and potentially bypass security checks focused on untrusted processes.
There are many injection techniques. On Windows, these include things like DLL injection, process hollowing, APC injection, etc. On Linux, we have analogous techniques: using ptrace to write shellcode into another process, LD_PRELOAD tricks, reflective injection of ELF libraries, or even abusing /proc/$PID/mem.
How this works in practice: A Linux malware might spawn a copy of /bin/ls or some harmless binary, then use ptrace to pause it and modify its memory to inject malicious code, then resume it. To the casual observer (or basic monitoring), the system just has an ls process running; meanwhile, that ls is doing something completely nefarious under the hood.
Real-world examples: - The Emotet trojan often injected into the running explorer.exe on Windows to hide its payload execution. - On Linux, the Turla group’s malware injected itself into the ssh process to stealthily exfiltrate data.
6. Binary Mutation (Shape-Shifting Malware)
The last category we’ll discuss is binary mutation, which includes techniques like polymorphism and metamorphism. These aren’t about runtime behavior so much as about malware continually altering its own code to avoid detection. It’s akin to a person changing disguises every day to avoid recognition.
There are different levels of mutation:
-
Polymorphic malware typically encrypts or encodes its payload and on each run (or each new copy) it generates a new decryption routine. The core malicious logic is hidden under encryption, and only a small decrypter stub is visible – which itself changes slightly every time.
-
Metamorphic malware takes it a step further by actually mutating the code of the payload itself (not just encrypting it). It can reorder instructions, swap in equivalent code, change registers – ensuring no two instances are identical in code fingerprint.
Historical example: The Storm Worm botnet in the late 2000s had a polymorphic packer that changed the binary every 30 minutes or so, foiling antivirus signature updates.
This technique makes signature-based detection largely ineffective. Even if security tools identify one variant, the next might look completely different while performing the same malicious functions.
Defending Through Behavior Detection
With so many evasion techniques, how can we defend our systems without extreme lockdown? The key lies in behavioral detection—watching what programs do rather than what they look like.
Linux provides several tools for behavioral monitoring:
1. System Auditing with auditd
Linux’s audit framework can log system calls and events based on rules you define. By configuring auditd, you can record things like every time a program is executed, or if a file in a sensitive directory is modified.
For example, you could set a rule to alert if any process calls the ptrace system call (since code injection via ptrace is unusual in normal apps), or if any new binary is executed from /tmp (since malware often drops files there).
Sample command to watch for ptrace use:
auditctl -a always,exit -S ptrace -k trace_monitor
2. Process and Memory Monitoring
Utilities like ps, top, or the more specialized ps_mem can help you spot strange processes or memory bloat. For instance, if you know roughly how much memory your usual applications use, a sudden spike in a normally small process could indicate something was injected into it.
3. File Integrity Monitoring
Tools like Tripwire create a baseline of cryptographic hashes for important system files and then monitor for changes. If malware tries to tamper with or replace a critical file (for example, inserting itself into your .bash_profile or altering an SSH binary), Tripwire can alert you to the modification.
4. Rootkit Detection
Since advanced malware often tries to bury itself, using a scanner like rkhunter (Rootkit Hunter) periodically is wise. Rkhunter checks for known rootkits and suspicious patterns – for example, it looks for hidden files, unexpected network ports open, or differences between system binaries and known-good hashes.
5. System Call Tracing
strace is a tool that can attach to a running process and log all system calls it makes. If you suspect a program is acting fishy, you can run it under strace (or attach after launching) to see exactly what it’s doing – e.g., opening files, creating processes, connecting to network sockets, etc.
If you open an unknown PDF and see it executing /bin/sh or accessing system files it shouldn’t, that’s a red flag.
6. Custom Scripts and Automation
You can create scripts that periodically check for suspicious conditions, like processes with writable-executable memory regions or files that have been deleted but are still running.
Practical Linux-Based Hardening Setup
Let’s translate knowledge into action with a multi-layered approach to hardening your Linux system:
1. Isolate Risky Applications with Firejail
Firejail is a user-friendly sandbox that leverages Linux namespaces and seccomp-bpf to restrict what an application can do. It essentially creates a lightweight “jail” around the app, limiting its access to your file system, network, and other resources.
For example, to run a suspicious PDF in isolation:
firejail --net=none --private evince suspicious.pdf
This will run the PDF viewer in an isolated environment with no network access and a temporary home directory. Even if the document contains malware, it’s trapped in that jail.
2. Enable Mandatory Access Control (MAC)
Modern Linux distributions often come with AppArmor or SELinux enabled. These are kernel security modules that enforce fine-grained policies on what processes can do. By taking the time to ensure these are in enforcing mode and tailoring critical profiles, you can prevent a lot of malicious behavior.
For example, AppArmor can confine a PDF reader so that it cannot execute child processes or write to sensitive directories. SELinux, when properly configured, can block a process from getting write+execute memory, which would prevent many injection techniques.
3. Use Network Isolation and VPNs
If you are intentionally running something potentially malicious (for research or curiosity), consider doing so with your network interfaces off or isolated. You can create network namespaces easily with Firejail using the --net=none option.
For everyday use, consider setting up outbound firewall rules with ufw or firewalld to restrict which applications can access the network.
4. Implement Regular System Scanning
Incorporate tools like rkhunter and chkrootkit into a routine (maybe via cron job or manual weekly runs). These tools will scan for known indicators of compromise.
Similarly, set up file integrity monitoring with Tripwire or a simpler open-source alternative to get alerted if critical files change unexpectedly.
Don’t forget the basics: keep your system updated and run periodic ClamAV scans to catch known malware signatures.
5. Analyze Binaries Before Execution
When you download a new or unknown binary, inspect it before running. Tools like checksec will tell you if the binary has NX, PIE, canaries, etc. If you see NX disabled on something you just downloaded, be wary – most modern compiled software should have NX enabled (i.e., not allow execution on the stack).
You can also use the strings command to look for suspicious content in a binary, or run ldd to check what libraries it depends on.
6. Set Up Live Alerts with auditd and inotify
Configure audit rules for critical events:
# Watch for execution in /tmp
auditctl -w /tmp -p x -k exec_from_tmp
# Monitor ptrace use (potential code injection)
auditctl -a always,exit -S ptrace -k trace_monitor
Use inotify to watch key system directories for changes:
inotifywait -m /etc -e create -e modify
7. Monitor for Memory and Process Anomalies
Set up a periodic job that checks for suspicious memory patterns, such as RWX (readable, writable, executable) memory regions:
sudo find /proc -type f -name maps -exec grep -l "rwx" {} \;
Also check for processes running from deleted files or memory-fd:
ls -l /proc/*/exe 2>/dev/null | grep -E 'memfd:.*\(deleted\)|\(deleted\)$'
Advanced Detection: Catching Fileless Malware
Let’s look at specific techniques to detect stealthy, fileless malware that tries to live only in memory:
1. Detecting Processes Running from Deleted or Memory-Only Files
One hallmark of sophisticated malware is running in memory without a file on disk. On Linux, when a process is started, the kernel keeps a link to the executable it’s running (accessible via /proc/
To check for such processes:
ls -l /proc/*/exe 2>/dev/null | grep -E 'memfd:.*\(deleted\)|\(deleted\)$'
If you find a process running from a memfd, this is highly suspicious. In a normally running system, you typically won’t see any such entry. So if you do see one, it’s a red alarm – likely an unauthorized or malicious process is running purely from memory.
2. Scanning for RWX Memory Regions
As discussed, no legitimate user-space process should have a memory region that is readable, writable, and executable at the same time (unless perhaps JIT compiling, but even then, modern JITs tend to mark as RW then flip to RX). An RWX memory segment is a potential indicator of injected or self-modifying code – essentially a hallmark of shellcode or JIT spraying.
To scan for such regions:
sudo find /proc -type f -name maps -exec grep -H "rwxp" {} \;
If you find a process with RWX memory, investigate it further:
cat /proc/[PID]/cmdline
cat /proc/[PID]/status
3. Monitoring memfd_create and Related Calls
To catch fileless malware as it happens:
# Set up auditd to watch for memfd_create
auditctl -a always,exit -F arch=b64 -S memfd_create -k memfd_watch
# Monitor execve calls with AT_EMPTY_PATH flag (used for executing memfd files)
auditctl -a always,exit -F arch=b64 -S execveat -F a2=0x1000 -k memfd_exec
In fact, tools like Falco have a rule for exactly this scenario: detecting execution from memfd memory. Falco’s rule (which uses eBPF under the hood) sets a condition proc.is_exe_from_memfd=true to catch when a binary is run from a memfd (fileless execution).
Example Detection Scenario
Let’s say you open a dodgy email attachment on your Linux laptop. It appears to do nothing. But you run our recommended ls -l /proc/*/exe | grep deleted check and find a /proc/24819/exe -> memfd: (deleted). You investigate PID 24819 – it’s running as your user, and lsof -p 24819 shows it has an IPv4 TCP connection to an unfamiliar IP and has the /usr/lib/x86_64-linux-gnu/libc.so open (typical of any process, since it uses libc).
Clearly, no normal user-space app should be running from a memfd. You could then:
1. Use gcore 24819 to dump its memory for analysis
2. Attach strace to see what system calls it’s making
3. Investigate what’s in the memory with strings on the core dump
4. Kill the process and investigate how it was launched
You’ve just caught fileless malware that evaded initial detection!
Conclusion: Fortify Without Fleeing
We’ve journeyed through the shadowy tactics of sandbox-evasive malware and emerged with a toolkit of strategies to counter them. The overarching theme is empowering you – the user of a “daily driver” Linux system – to fortify your machine without abandoning convenience or usability.
By implementing practical measures – from sandboxing apps with Firejail, to enabling AppArmor/SELinux, to monitoring for behavioral tell-tales – you create multiple lines of defense. None of these measures alone is a silver bullet, but together they make your system a tough nut to crack.
The tone we set at the start was a dare: “Infect me if you can.” After this deep dive, that dare isn’t a bluster – it’s a calculated challenge. We’ve seen how to systematically strip malware of its usual advantages: if it waits, we’ll watch longer; if it hides in memory, we’ll scan there; if it checks for no user, we’ll simulate activity; if it mutates, we won’t rely on static fingerprints.
Security done right enables freedom – the freedom to dare malware and attackers with confidence. So go ahead, harden your system, and let malware know it picked the wrong target. Your daily driver isn’t a vulnerable playground – it’s a fortified fortress with an owner who knows its every nook and cranny.
Challenge issued, and with these defenses, challenge accepted!
Note: The techniques described in this article are meant for defensive purposes. Always adhere to legal and ethical boundaries when experimenting with security tools.